VA.gov
🎒 the background.
During my tenure at Clarity, I am working within the platform team for the Department of Veterans Affairs to help build VA.gov. I serve as a Frontend Engineer on the Identity team, which is an amalgam of Authentication, Authorization, and Identity Access Management (IAM). We act as gatekeepers for what a user is and what they can access every time they sign in at VA.gov. Because our team is so unique we work on a variety of challenges to build different services, applications, and internal tooling for other platform teams and VA.gov users alike.
It is hard to encapsulate all of the tasks and tooling I have worked on during my time with the VA but here is an outline of things I worked with my team on.
⚙️ the problems.
Unable to search for test users
- Have to search in Github for mock users within a huge Markdown file
- Outdated user information including services and passwords
- No definitive way to see if the account is being used
- No way to view accounts without being on VA.gov’s network
Signing in
- Dependent on 2nd-party teams for SAML integration
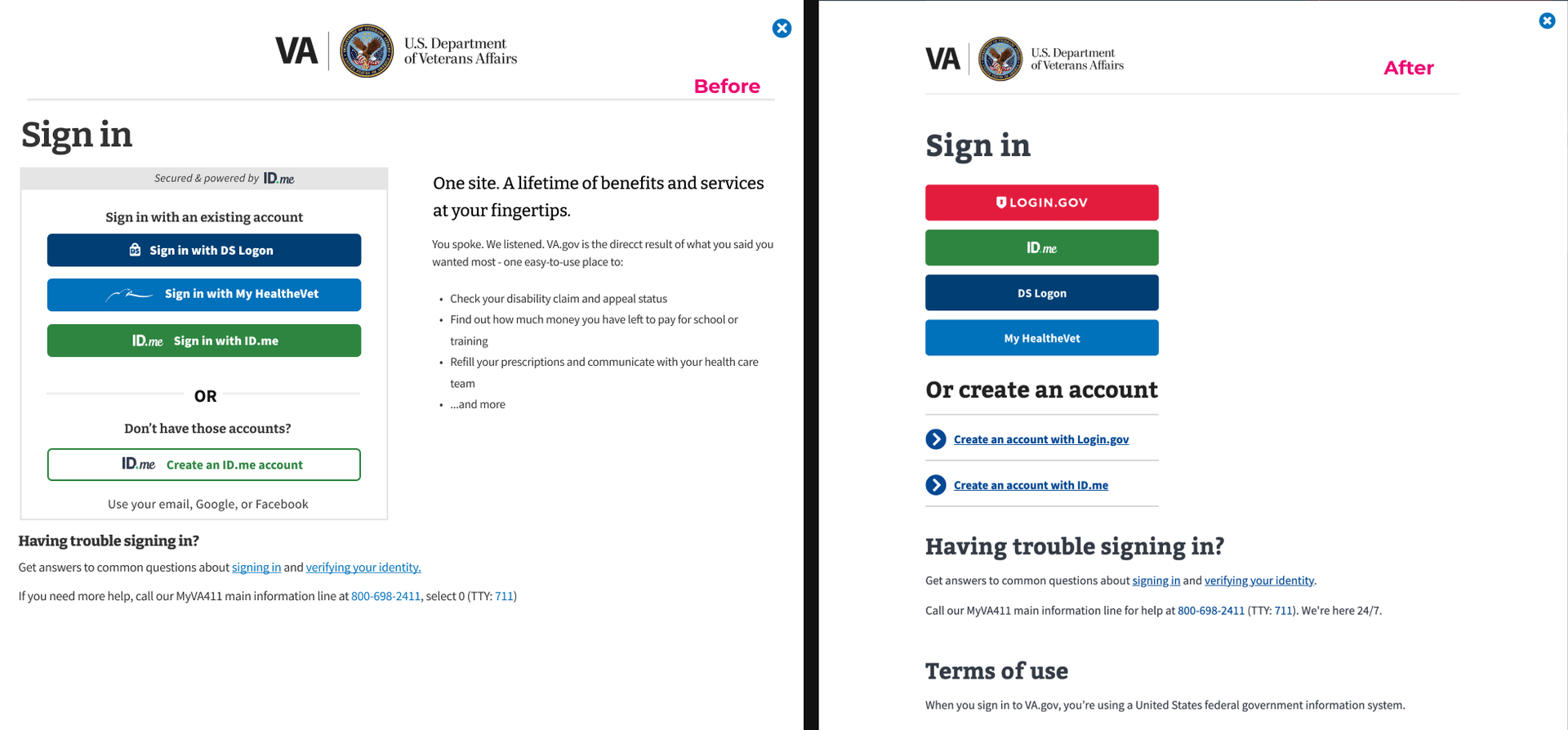
- User sign in flow takes too long (27 redirects)
- The sign in modal user flow causes cognitive overload
Mocked authentication
- Unable to programmatically create mocked users
- Prevented from signing in when Credential Service Providers (CSPs) are down
Integrations
- No integration with VA’s flagship mobile application
- Secondary partners like eBenefits and My HealtheVet have different sign in flows
Fraud Prevention
- Detecting fraud after the fact
✅ the results.
Creation of a dashboard to manage mock user credentials colloquially known as the Test User Dashboard
- Creation of automated tasks that transform Markdown to SQL (Postgres)
- Creates the ability to sort, filter, and search for test users credentials across environments domain
- Setup authentication using OAuth and Github repo groups for access management without requiring them to be on the VA.gov internal network
Creation of an in-house OAuth 2.0 authentication microservices framework
- Integration of OAuth 2.0 web + mobile on VA.gov with cookie-based tokens
- Implement secure session management with active refreshes
- No impact to original SAML’s Single Sign-On capability
Improve VA.gov for every user
- Increase speed of user flow by decreasing redirects from 27 down to 7 using OAuth
- Decrease cognitive overload by applying user research data in the redesign of sign in applications (modal and page)
- Creation of a flexible, configuration-based authentication for secondary partners that allows the usage of SAML or OAuth
- Real-time fraud detection to allow bank account changes to be programmatically reviewed. The DigitalVA Expo recently spoke about our work in combating fraud (opens in a new tab).
🦄 the prototypes
📲 in the media
- Preventing and detecting fraud in real time (YouTube, starts at 38:20)
- Implementing authentication with the Login.gov Credential Service Provider (YouTube)
- Enabling authentication on VA Flagship Mobile (Adhoc Blog, 2022)